Summary
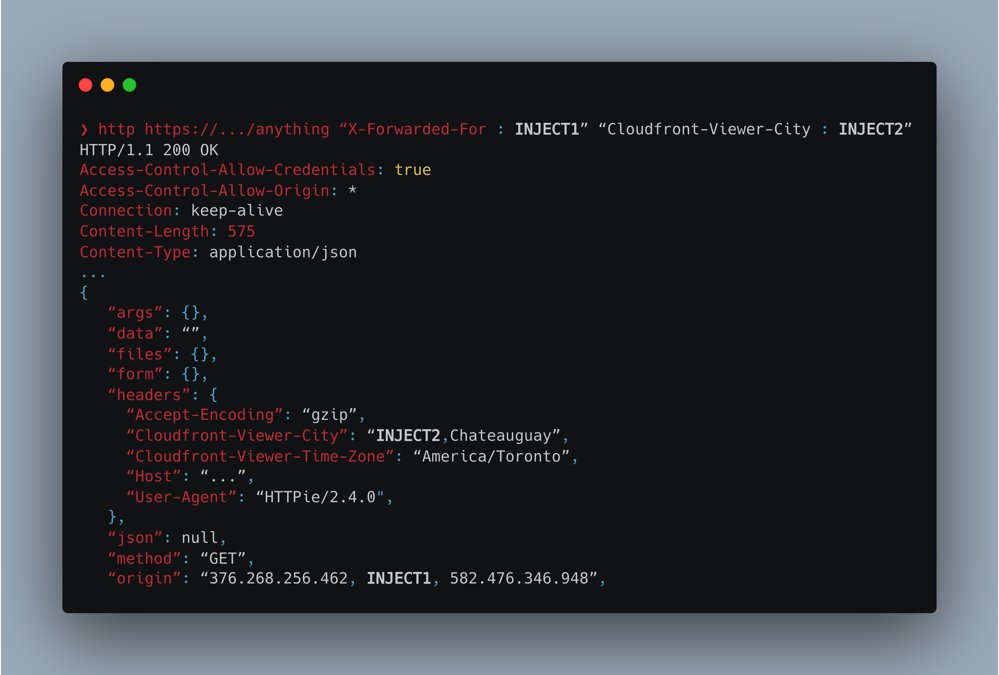
Executing Cloud Functions or Cloud Run in any project and in any organization allowed bypassing the GKE Authorized Networks (aka Kubernetes
control plane firewalls) of a cluster in a different project or organization.
Affected Services
GKE
Remediation
Run the following command on existing clusters to block traffic to the GKE control plane from Google Cloud VMs or Cloud Run sourced with
Google Cloud public IPs (the same flag can be used at cluster creation time as well): `gcloud container clusters update CLUSTER_NAME --no-enable-google-cloud-access`
Tracked CVEs
No tracked CVEs
References
https://cloud.google.com/blog/products/identity-security/updates-coming-for-authorized-networks-and-cloud-runfunctions-on-gkehttps://cloud.google.com/blog/products/containers-kubernetes/understanding-gkes-new-control-plane-connectivityhttps://twitter.com/itspeterc/status/1534205155914264576https://twitter.com/itspeterc/status/1578054948188819457
Contributed by https://github.com/mer-b
Entry Status
Finalized
Disclosure Date
Wed, Mar 9th, 2022
Exploitablity Period
Until 2022/09/30
Known ITW Exploitation
-
Detection Methods
-
Piercing Index Rating
-
Discovered by
Peter Collins